BSI-Standard 200-2: IT-Grundschutz-Methodology
The BSI-Standard 200-21 provides a methodology for the effective implementation and management of information security. The standard complements BSI-Standard 200-1 and thus aligns with ISO/IEC 27001.
Whereas 200-1 only describes general methods for initiation and management of an information security management system (ISMS), 200-2 provides concrete guidance for its practical implementation. It does so by introducing three distinct protection levels, tailored to the specific risk profile of an organization:
| Protection Level | Description | Pros | Cons |
|---|---|---|---|
| Basic Protection | Broad and initial safeguard for organizations just getting started with IT-Grundschutz, with no significantly increased risk. | low effort, quick to achieve | only a low level of security |
| Core Protection | Targets business processes and assets exposed to specific security risks; focuses on securing what is essential to operations. | focuses on crown jewels2 | may overlook other vulnerabilities impacting overall security |
| Standard Protection | Classic IT-Grundschutz approach for organizations where security incidents would result in financial loss or productivity impact; assumes sensitive data handling. | highest level of protection, considers all assets | high implementation and maintenance effort and cost |
Security Policy
The standard provides guidance on how to achieve these defined protection levels within an organization and outlines how to document then in a Security Policy. The policy should include
- the scope of the policy
- the security objectives
- the overall strategy to achieve the protection level
- the organizational structure of the ISMS
Systematic Approach
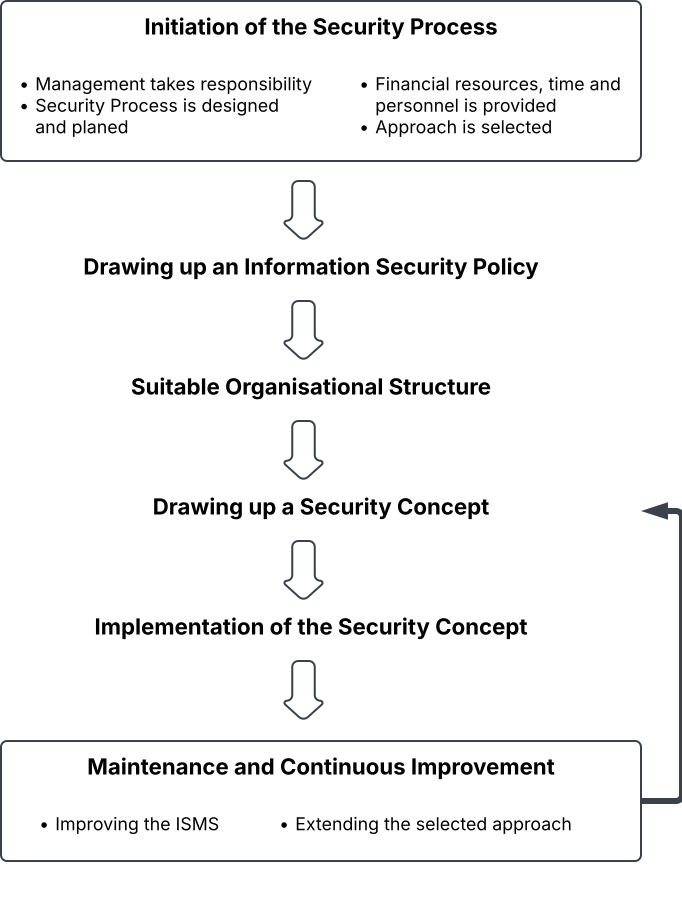
In order to establish the ISMS in an organization, BSI 200-2 proposes a systematic, multi-stage approach, as illustrated in Figure 1.
The figure also highlights the Plan-Do-Check-Act-cycle3 as part of an iterative methodology, underlining the need to continuously re-evaluate both potential risks and the effectiveness of available ISMS controls. Accordingly, the security concept must be audited at regular intervals - or reactively in response to specific system compromises.
Initiation of the security process
The process must be initiated by the organization's management. As the standard emphasizes, it is essential that the management demonstrates its commitment to the ISMS - this includes delegating responsibilities and providing adequate financial and human resources for both planning and implementation.
Drawing up of an Information Security Policy
The Security Policy serves as an "essential basis for the design of the security process" and defines both the security objectives and the level of protection targeted by the organization. As a means to raise awareness within the organization, the policy also includes the rationale behind the security efforts. Furthermore, it specifies the safeguards and structural measures intended to achieve the defined protection level.
Design of a suitable organisational structure
To effectively steer and manage the ISMS, a suitable organizational structure has to be established. This includes appointing an Information Security Officer, who serves as the "main contact person [...] for all aspects of information security". The role includes managing the security process, coordinating related tasks, and reporting directly to management on all security-related issues.
Drawing up of a security concept
The security concept is developed on the basis of the modules provided in the IT-Grundschutz Compendium. BSI-Standard 200-2 emphasizes that when protection requirements are significally higher, a risk analysis should be conducted. The risk analysis can be carried out following the guidance of BSI-Standard 200-3.
Implementation of security concepts
The necessary safeguards to mitigate the identified risks are implemented in order to achieve the intended level of protection.
Maintenance and continuous improvement of information security
The security process and the implemented safeguards must be regularly re-evaluated - both at predefined intervals and in response to security incidents or system compromises. The effectiveness of the safegaurds should be assessed in this context, which may lead to the removal of ineffective or unnecessary measures, the addition of new ones, or adjustments to the organizational structure of the ISMS.